ARE YOU A BEST KEPT SECRET COACH READY TO BE DISCOVERED?
Helping Top Entrepreneurs Get the PR To Become the #1 Authority in Their Industry
We Turn Nobodies Into Celebrities, Entrepreneurs Into Thought Leaders,
And Ordinary Social Media Users Into Verified Influencers.
As Seen On






If you’re an Expert Coach, Author or Realtor
Who want to dominate google by Getting Featured (Publicity) on Major Publication to position yourself as industry thought leaders and stand out from the competition to take your brand to the next level of success.
Then I have a solution for you.
We Helping Entrepreneur, Experts & Coaches Expand Their Authority. Reach. Fame. Recognition. Influence. Profits.
We Help You Achieve All Of These !
Do you know?
- 92% of consumers prefer earned media than traditional ads.
- These days, Millennials are prone to be influenced by blogs, news, magazine, podcast and social networks.
- 80% of decision-makers prefer getting data from articles instead of from ads.
- 70% of consumers prefer to know a company from an article rather than from an advertisement.
- 68% of consumers are inclined to read information about a company they are interested in.
- 86% of people have a tendency to avoid TV ads.
Your Authority Influences Buying Decisions Both Online & Offline
It’s a fact that people buy more and more often from people they trust. Showcasing your industry expertise will gain you instant credibility.
Be The Leader In Your Field
We will move you or your brand 5-10 years forward, accelerating the growth process that in most cases takes a whole lifetime, infinite trials and disappointments. In few weeks you’ll become an authority everybody want to connect with.
From Media Placements To Social Media Verification. We Provide A Range of Unique Services You Need To Become Recognized Leader or Turn Your CEO Into One.

Media Placements (Publicity)
People are talking about you online and We believe you should lead the conversation. Win media coverage to boost your brand.
Our team has secured over 1,000 media placements on top-tier publications. Getting your achievements or your lifestyle Mention on a renowned big publication such as Yahoo Finance, Yahoo News, Marketwatch, Grind Success and 100+ other. They have gone on to build strong personal brands, and they have been strategically positioned as leaders in their industries.

Magazine Cover Placements
Are You looking get featured on the magazine cover feature?
Our team will help you and your brand to get in magazine cover placements to give you or your brand more visibility online.

Google Knowledge Panel
A Google Knowledge Panel is so important because it’s the first thing that anyone sees when they search your name or your company name on Google for the rest of your life. This google panel will include a picture of yourself, a short bio, a date of birth, businesses owned and links to your main social media platforms.
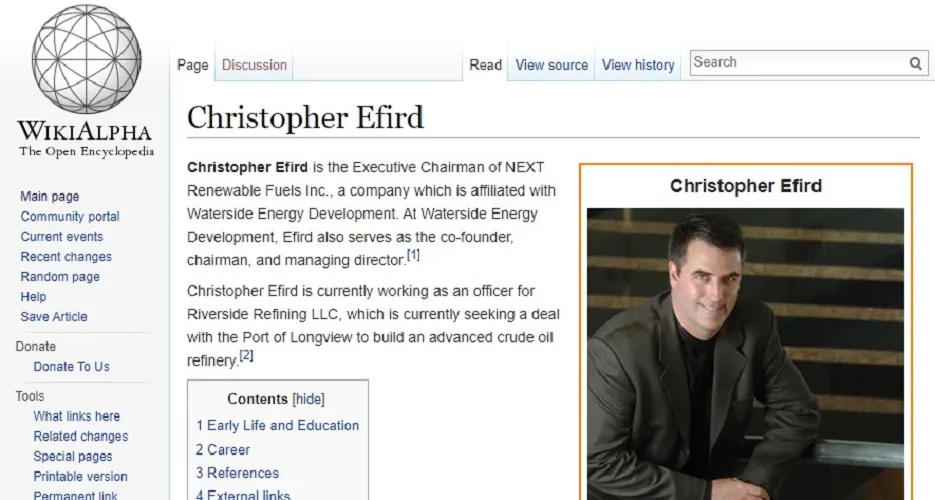
Wiki Pages Creation
Public Relations & Brand Image based on press placement establish how Notable and Newsworthy of a Public Figure you are on Google. RankFame press placement will dramatically increase your chances of Wiki Pages . Boosting your reputation with appearances in online publications is the foundation of the journey to credibility.

IMDb Page Creation
IMDb is one of the oldest websites on the internet, and everyone is familiar with it. It’s a place reserved exclusively for celebrities, and people who are famous in any respective field, whether it’s acting, or direction, or music composition. Over the years, we have mastered the art of IMDb page creation.
It ranks high on Google, and it will take your brand credibility to the next level.
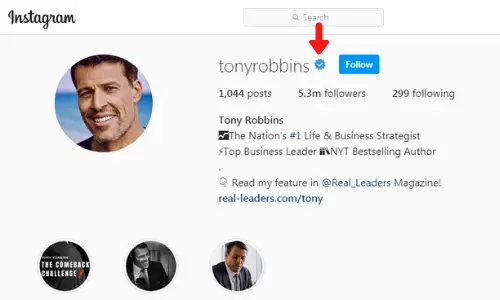
Social Media Verification!
Ever dreamed of getting that blue check mark on Facebook or Instagram? Who hasn’t. That blue check mark is not just a simple tick. It’s a sign of credibility, authority and influence. Only the most renowned brands and influencers are able to get that coveted blue check mark.
We help you get verified by Instagram or Facebook. We help you meet the eligibility requirements. Our agency will handle your account and file your application.

Get Into INC Magazine
Want to be seen on your company on Inc.com? we will help you to add your business to Inc Magazine.

Guest Blogging
PR and guest blogging are two faces of the same coin. When it comes to guest blogging, every single article will be SEO optimized so that you can rank on Google and other search engines as well. Boost your website traffic by increasing your brand’s visibility on Google, Yahoo, Bing, etc. Since relevant keywords are used in the articles, countless new people will find your brand at the top of the search results.

Personal Branding Strategy
Is your personal brand practically non-existent? Does nothing about you show up when people Google your name? Are you finding it difficult to close deals or expand your business, because people don’t think you’re credible enough? That means its time you build a personal brand for yourself.
Our Team help you to build a world class personal brand to Establish a Go-To brand in your industry!
“A Good PR Story Is Infinitely More Effective Than A Front Page Ad.”
— Sir Richard Branson
Over the past 6 years we have worked with over...

of the world’s top CEOs and entrepreneurs to help them build their brand’s online and establish credibility into our own high ticket program, and do what we’ve learned to helped hundreds of entrepreneurs.
Being a member of our Authority Accelerator has been a game changer for many high level entrepreneurs just like you.
Publicity= Low cost and high credibility
Here is Some of our clients we help them build their brand presence on google:

Jeff Lopes

Tonye Irims

George Dfouni

Fabrice Sopoglian

Eduard Soponar

Jason Greer

Christopher Massimine

Arpit Sharma
"The Secret Sauce to Successful Marketing is to Build a Brand that is Distinct from your Competition."
Our Clients Are Consistently Featured On Some Of The Most Elite Publications
Here are few of the publications we work very closely with














“Invest in yourself, so others will invest in you„

Hi, I'm Aariya Rafi!
A Passionate Entrepreneur, Author & PR Maverick.
I’ve Worked With Six-Figure entrepreneurs like George Dfouni, Jason Greer, Jeff Lopes, LaVern McCants and many other Successful Entrepreneur like Yourself.
And Help them Become the Trust-worthy Authority in Their Industry & Dominating Google First Page to Attract More High-Ticket Pre-Qualified Lead and Generate More Revenue.
My works has appeared on ThriveGlobal, GoodMenProject, TECHco, Disrupt Magazine, HackerNoon, Dzone and other Top Tier Publications as a Thought Leader in Creating a Digital Footprint by Using Different Marketing Techniques.
Besides, I am the Editor-In-Chief at GrindSuccess, an Entrepreneur Magazine.
Through my experience and talking to author – entrepreneurs, I know that PR is the best tool to help you educate your potential clients on your philosophy and get High Paying Pre-Qualified Leads, who are ready to working with you.
So, What are you waiting for?
YOU FOUND US ON GOOGLE, RIGHT?
Google consistently ranks us as one of the top PR agencies around.
We've Worked With Industry Leading Brands
World’s leading brands like these are trusting us and getting our help to grow their businesses online. Here are few of them.








Why You’re Correct In Investing In PR

Timelessness
Getting your achievements or your lifestyle Mention on a renowned publication is something that you can benefit from for years and years. It literally outlasts advertising.

Credibility
PR adds major credibility to your personality and your business, which gives your clients, sponsors, future rockstar employees, and would-be partners more confidence in investing in you.

Growth
Whether you need more users, more customers, more clients, more employees, or more capital, the right PR is a great tool to fuel growth.
PR Will Increase The Chances To
Build Your Brand Authority!
Skyrocket Rankings!

Social Media Verification!
Google Knowledge Panel
Wiki Pages
Get Pre-Qualified Lead
Keep your eye on our blog to get upto date
Payment
With a signed agreement to ensure a Secure, Guaranteed and Speedy process for both parties.







